In the digital age, where email serves as a primary communication tool for businesses, the threat of phishing scams looms larger than ever. These sophisticated and deceptive emails are designed to trick employees into giving away sensitive information, leading to potential financial loss and data breaches. Understanding the most common types of phishing scams is the first step in fortifying your defenses against them. Let’s dive into some of the most prevalent phishing tactics and how you can safeguard your business against them.
Introduction
You and your team might be well-versed in the basics of identifying phishing emails, but can you recognize the signs of a more sophisticated attack? The frequency and complexity of phishing scams targeting employees are on the rise. We’re spotlighting the most cunning and successful phishing emails circulating today. Familiarize yourself with these examples, share this knowledge, and fortify your defenses.
Basic Protection Techniques
- Enabling security measures like 2FA, where-by a code is required to complete login, as well as ensuring you’re using different passwords for different sites will limit any impact if you do accidently get phished. 2FA will ensure an attacker can’t log in even with your username / password and having separate logins means that getting access to one account doesn’t expose all your accounts with the same credentials.
- Ensure your email security is setup correctly to filter spam and quarantine suspected emails. Using technology in Microsoft365 allows for links to be rendered safe (SafeLinks) and for suspected Phishing emails to be marked by Outlook to raise user awareness.
- Make sure all your workstations have up-to-date anti-virus and anti-malware software installed. This can prevent any accidentally downloaded malicious software from running and infecting your machines.
- Running phishing training and simulations with your users can help educate staff on what to look out for as well as providing a safe way to test and make sure your reporting systems are working effectively.
- Using a platform such as RiskBuddy allows for micro-training if there is a link clicked or user credentials compromised. Don’t punish users who do accidently fall for phishing training, but instead take advantage of the opportunity to provide additional training and how to report / spot suspected phishing attempts.
9 Common Phishing Attempts
1. The Fake Invoice Scam
Starting with a classic, the fake invoice scam preys on the urgency and fear of its recipients, prompting them to pay for services or products they never purchased. This technique is particularly effective against finance departments but can deceive anyone unaware of its signs.
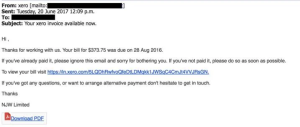
This email attack usually goes to finance departments, and can also take the form of a more targeted attack against a specific person in the finance team or a request from the ‘CEO’ to make an immediate payment.
2. Email Account Upgrade Scam
This scam exploits the fear of losing access to one’s email account, masquerading as an urgent update notice from familiar providers or even your own IT department. The sophistication of this scam lies in its appearance of harmlessness, urging users to verify personal details via a seemingly secure link.
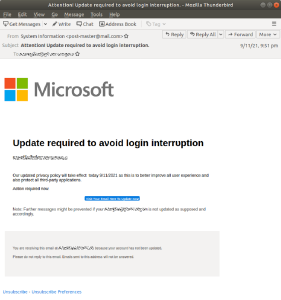
Nothing harmful stands out from this email. There are no obvious errors, no elaborate requests, the link itself would appear to direct to a safe “https” web page to an unsuspecting user, and it seems like a legitimate request to upgrade your account. A useful tip is to hover over the link itself when being asked to give personal details – as the text itself often doesn’t represent the true destination of the link which will appear when you hover over it.
3. Advance-Fee Scam
An oldie but a goodie, the advance-fee scam entices victims with promises of large sums of money in exchange for their banking information. Despite its outlandish premise, its longevity speaks to its effectiveness.
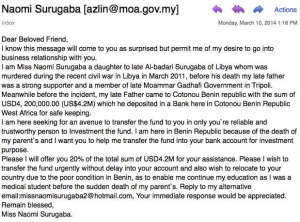
The scammer will offer you a large sum of money in exchange for your bank details usually under the guise of requiring the money to setup a transaction back to you, pay for legal fees, or settle a fine so the money can be accessed. Not only will you not receive a dime from this kindly Prince, but you will also see a chunk of your money go in the opposite direction.
4. Google Docs Scam
The Google Docs scam adds a layer of deceit by appearing to originate from someone you know, asking you to view a document. This scam is particularly insidious as it leads to a fake login page, aiming to capture your Google account credentials.
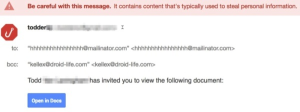
This sophisticated email encourages you to click on its link in order to view a ‘document’, which then takes you to an almost identical version of Gmail’s login page. Once an account has been selected, you’re then invited to grant access to your Google account which will give an attacker access to your Google account including your Gmail inbox. With access to your emails an attacker is then able to move horizontally into other accounts by resetting passwords, searching your inbox for login information and personal information.
5. PayPal Scam
Given PayPal’s vast user base, it’s a prime target for phishing attempts. These emails often create a sense of urgency about a problem with your account, complete with official logos and fine print, to trick you into revealing sensitive information.
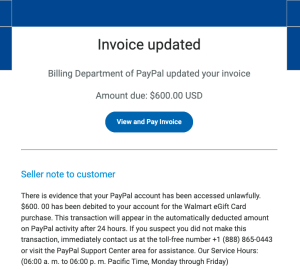
These emails a convincing chunk of fine print at the bottom of the email. Trying to enforce panic mode into its victims, often with a “There’s a problem with your account, please click here to fix it” kind of message. This tries to get users to click the link before they can think about what the email looks like or says.
6. Message from HR Scam
The trust placed in HR communications makes this scam especially dangerous. Emails claiming to be from HR may ask for personal information or prompt you to click on malicious links or attachments.

An HR email scam often contains a malicious attachment or link that, once clicked, will install malicious software onto your computer or device. If you receive a suspicious email like this you’re best off contacting your HR department outside of the email (call them directly or use an internal messaging system) to verify the request.
7. Dropbox Scam
Utilizing Dropbox’s popularity, scammers send emails urging users to click on a link to access a large file, leading to a counterfeit Dropbox login page designed to steal credentials.
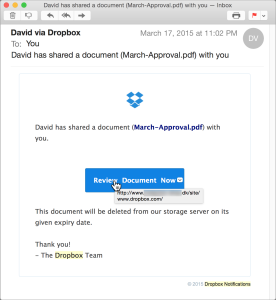
Clicking the link in these emails will take you to a page which is designed to look like the DropBox login page, the URL may also be similar with just a slightly different address or ending (.xyz for example rather than .com). Filling in your login details will provide the scammers with your Dropbox account details, you may even be logged into the real Dropbox after filling in the form so that you’re unaware you’ve been compromised.
8. The Council or HMRC Tax Scam
Preying on concerns about council tax, this scam employs various messages to trick recipients into divulging personal details under the guise of offering refunds or rebates for council tax overpayments.

The HRMC and council tax scams are quite prevalent and the UK Government has posted some advice on what to look out with these scam emails:
- It insists you’re in the wrong Council Tax band and are owed back payments on your Council Tax bill, when in fact your band is correct
- It says they’re from the local council or Valuation Office Agency (VOA) and ask for your bank details so they can provide a refund
- Claim that the VOA charges you to challenge your Council Tax band
- Claims that taxpayers must, by law, be represented by an agent to challenge their band
If you’ve received an email, text message or phone call about tax make sure to look up the official number for HMRC or your local council from their website and call them back. Don’t discuss the account the account or provide account information from an unsolicited phone call or email.
9. Unusual Activity Scam
Alerts about suspicious activity on your account are designed to panic recipients into acting hastily, often leading them to fraudulent websites where their information can be compromised.
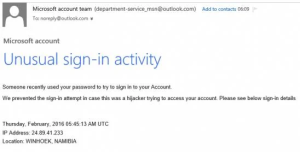
An unusual activity scam email can come from any app, website or platform – whether it be your bank or even your Instagram account.
Beyond Recognition: Taking Action
Identifying phishing scams is crucial, but it’s only part of the solution. To effectively protect your business, it’s vital to educate employees on recognizing subtle signs of phishing, reporting potential scams, and practicing safe online behavior. Explore our comprehensive library of phishing templates to arm yourself and your team against these digital threats.
As phishing scams become increasingly sophisticated, staying informed and vigilant is your best defense. By understanding the tactics used by cybercriminals and fostering a culture of cybersecurity awareness within your organization, you can significantly reduce the risk of falling victim to these malicious attacks.
